Account Takeover Isn’t a Password Problem — It’s an Identity Problem
Credentials are easy to steal. Verified identity isn’t. Our recovery flow verifies the person (not just the password) giving you what you need: no PII, no support burden, and a consistent process across platforms.






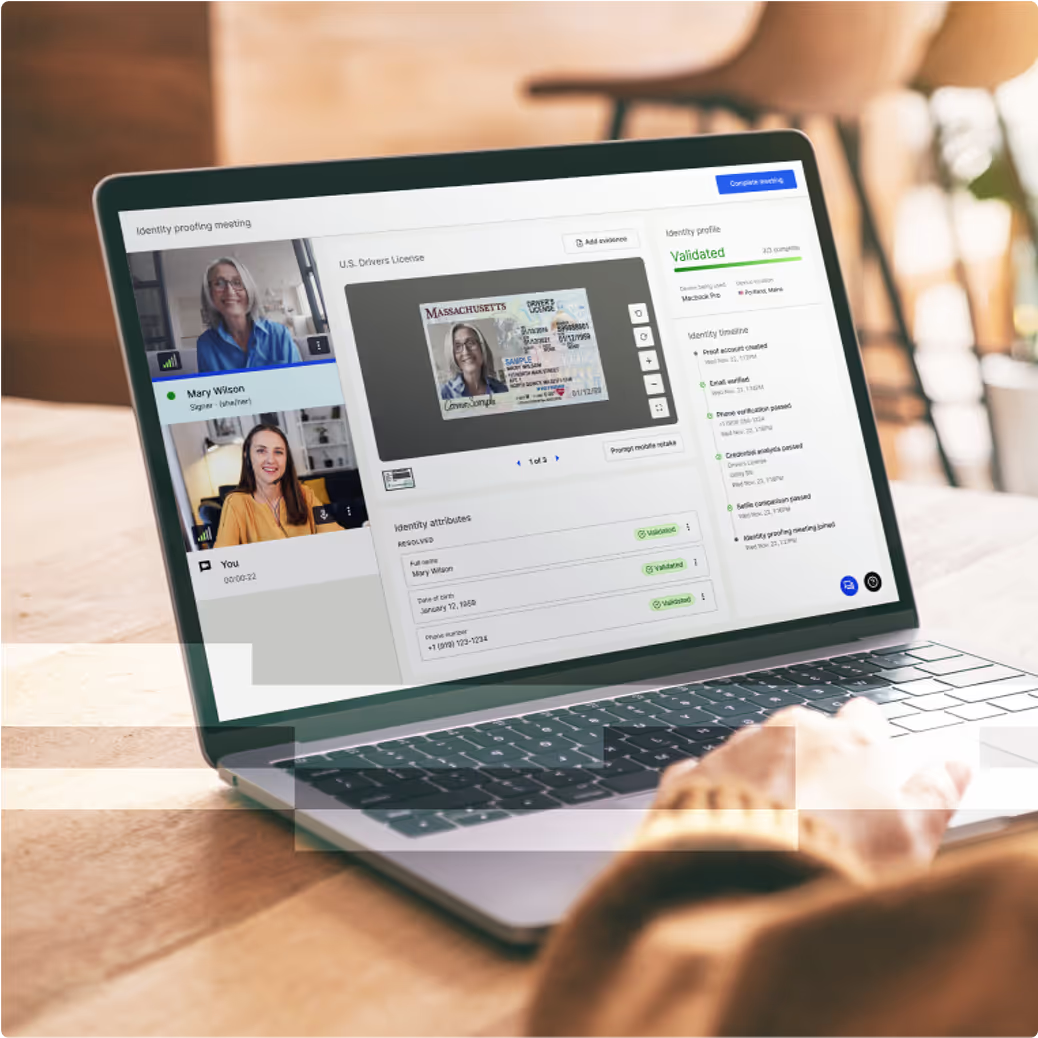
Account Recovery Built on Verified Identity
With Proof, recovery isn’t about credentials. It’s about verifying the person and returning a clean, trusted signal.

1. The user is redirected to recovery
Suspicious login or reset attempts are routed out of your environment into our recovery service.
2. We verify identity
Fraud signals, biometric checks, and human-in-the-loop review confirm whether it's really your customer.
3. We handle support
If the user needs help, they call us - not your team.
4. You get the result
You receive a simple, standardized recovery signal that tells you it's really them, without ever touching their PII.
Partnering with Proof allows us to uniquely ensure identity-assured transactions for contracts, authorizations, forms, and high-risk financial events across various sectors. Our strategic visions are perfectly aligned, and together, we’re poised to redefine the standards of what’s possible.


Learn how to stop account takeover by making recovery about identity, not credentials.
Stronger Recovery Means Safer Data and Fewer Calls

Real customers get in
Imposters are blocked, trust is preserved

You never touch PII
All sensitive data stays with us, so regulatory risk stays low

We handle support calls
Customers get help without adding to your support load

You align with peers
Recovery is standardized across leading platforms






Frequently asked questions
How long does it take to implement Proof?
Most teams are up and running in under a week. We don’t require any rip-and-replace; Proof fits into your existing systems and processes with minimal lift
Is Proof compliant with state and federal requirements?
Yes. Proof meets or exceeds all state and local requirements for remote online notarization (RON), identity verification, and electronic signatures, and is accepted in all 50 states.
How does Proof verify user identity?
When an account recovery request is made, the user is routed to Proof’s external recovery service. We verify the person using government-issued ID, facial biometrics, fraud signals, and human review when needed. Customers call us, not your support team, and you receive only a verified recovery signal — never their personal data. This makes recovery both secure against account takeover and consistent with how other leading platforms handle it.
Security doesn't have to sacrifice customer experience.