When Account Recovery Decides Trust
Fraudsters don’t need to crack logins to win. They trigger resets, impersonate users, and slip through recovery flows that favor the wrong person.
Proof makes recovery a strength instead of a weakness. By authorizing identity, not just credentials, we ensure accounts are restored for the rightful customer, every time.

Account Recovery Built on Verified Identity
Recovery is where trust is won or lost. Proof verifies the person, not just credentials, so imposters are stopped and real customers get back in.

1. Recovery redirected
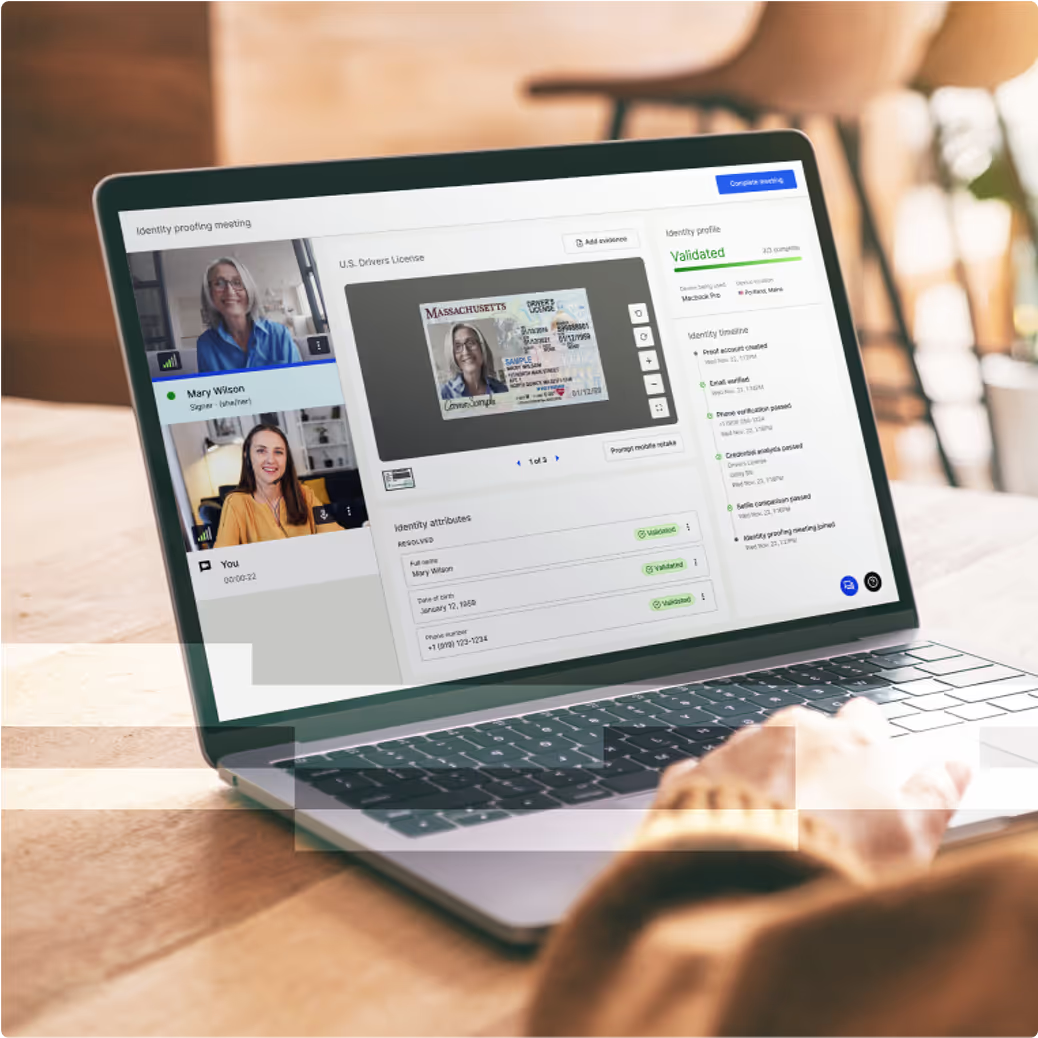
When recovery is triggered, customers are routed to Proof for identity verification.
2. Identity confirmed
Government ID validation, liveness checks, and fraud signals confirm the user is real. For edge cases, Verify offers human-in-the-loop identity reviews.
3. Signal returned
Institutions receive only a yes/no recovery decision — no PII, no support exposure.
4. Access restored
Legitimate customers regain access quickly, while impostors are stopped cold.
Partnering with Proof allows us to uniquely ensure identity-assured transactions for contracts, authorizations, forms, and high-risk financial events across various sectors. Our strategic visions are perfectly aligned, and together, we’re poised to redefine the standards of what’s possible.


Prevent account takeover damage by tying recovery to verified identity instead of credentials.
Outcomes That Built Trust
.png)
For your customers
- Faster recovery without added friction
- Confidence that accounts are always restored in their favor

For your teams
- No exposure to sensitive PII
- Fewer escalations and manual reviews

For your business
- Reduced fraud losses and chargeback costs
- Defensible audit records for regulators






Fraud and impersonation move fast. Recovery has to be faster.
Frequently Asked Questions
How long does it take to implement Proof?
Most teams are up and running in under a week. We don’t require any rip-and-replace; Proof fits into your existing systems and processes with minimal lift
Is Proof compliant with state and federal requirements?
Yes. Proof meets or exceeds all state and local requirements for remote online notarization (RON), identity verification, and electronic signatures, and is accepted in all 50 states.
How does Proof verify user identity?
When an account recovery request occurs, the user is routed to Proof’s recovery service. We verify identity with government-issued ID, facial biometrics, fraud signals, and human review if needed. Customers interact with Proof, and you receive only a verified recovery signal — never their PII.
